Understanding the Security Risks of Compressed Uniform Resource Locators (URLs)
In the digital age, Uniform Resource Locators (URLs) serve as the addresses that allow us to access websites and online resources. However, certain security concerns arise when dealing with compressed URLs. This article aims to shed light on the security issues associated with compressed URLs, providing valuable insights into the potential risks and how to mitigate them. By exploring these vulnerabilities, users can make informed decisions to protect their online activities and data.

What security issue is associated with compressed uniform resource locators?
1. What are Compressed URLs?
- Briefly explain what compressed URLs are, highlighting their purpose of shortening long URLs for convenience and ease of sharing.
- Discuss the popularity and widespread use of compressed URLs in various online platforms and services.
2. Understanding the Security Risks
- Introduction to Security Risks: Explain the potential vulnerabilities and risks associated with compressed URLs, emphasizing the need for caution.
- URL Obfuscation: Discuss how compressed URLs can be used to hide malicious or phishing links, tricking users into accessing harmful websites.
- Link Spoofing: Highlight how compressed URLs can be manipulated to redirect users to fraudulent websites that mimic legitimate ones.
- Social Engineering Attacks: Explain how attackers may exploit compressed URLs to deceive users into divulging sensitive information or performing malicious actions.
- Malware Distribution: Discuss the possibility of compressed URLs being used as vehicles for spreading malware and initiating cyber attacks.
3. Mitigating the Risks
- Be Cautious with Clicking: Advise users to exercise caution when clicking on compressed URLs, especially from unfamiliar or suspicious sources.
- Hover over Links: Encourage users to hover their mouse over a compressed URL to reveal the full expanded URL before clicking.
- Verify the Source: Emphasize the importance of verifying the legitimacy and trustworthiness of the source before accessing a compressed URL.
- Use URL Expander Services: Recommend the use of reputable URL expander services that can reveal the original full URL behind the compressed link.
- Install Security Software: Suggest the installation of reliable antivirus and anti-malware software to detect and block potentially harmful compressed URLs.
4. Best Practices for Safe Internet Browsing
- Keep Software Updated: Highlight the significance of keeping web browsers, operating systems, and security software up to date to benefit from the latest security patches.
- Be Aware of Phishing Techniques: Educate users about common phishing techniques and how to recognize suspicious emails, messages, or links.
- Employ Strong Passwords: Remind users to use strong and unique passwords for their online accounts to prevent unauthorized access.
- Enable Two-Factor Authentication (2FA): Encourage the use of 2FA as an additional layer of security to protect online accounts.
- Regularly Back up Data: Stress the importance of regularly backing up important files and data to prevent loss in case of a security incident.
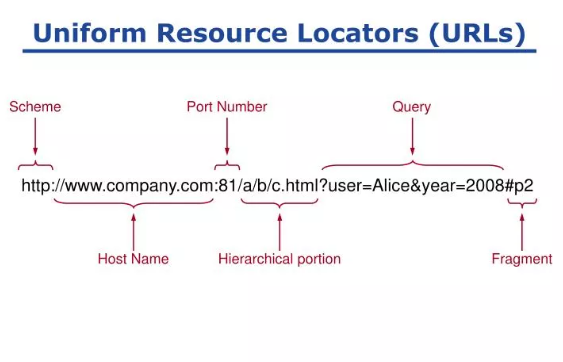
Uniform Resource Locator
While compressed URLs offer convenience and simplicity, they also pose certain security risks. It is crucial for users to be aware of these vulnerabilities and take necessary precautions to protect themselves online. By understanding the risks associated with compressed URLs and implementing best practices for safe internet browsing, users can minimize the chances of falling victim to malicious activities. Remember, staying informed and proactive is the key to maintaining a secure online presence in today's digital landscape.